Industrial Control Systems (ICS)/Operational Technology(OT) Security Homelab: Part 1 - Design
Designing an ICS/OT Security Homelab Link to heading
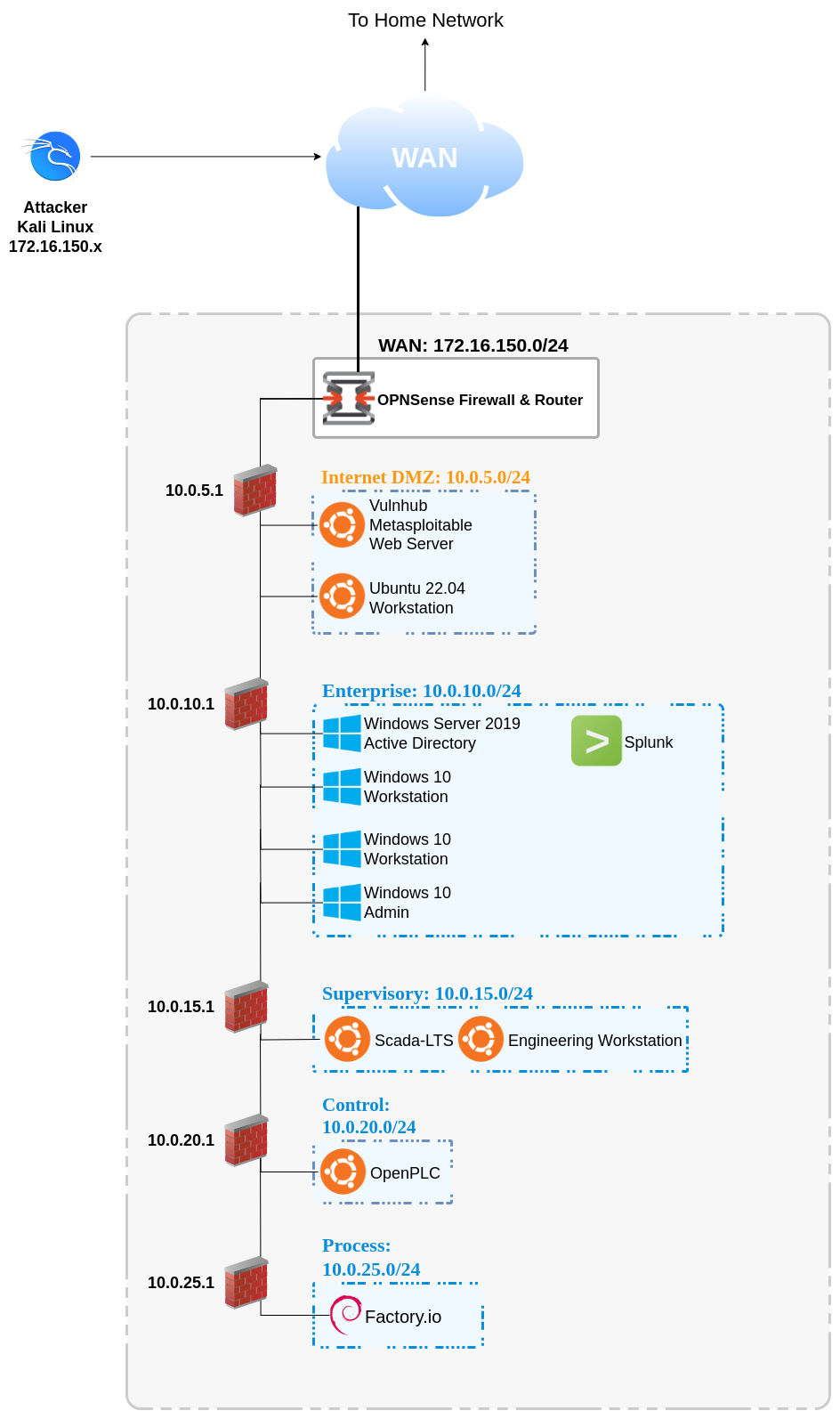
I have been procrastinating about documenting my security lab, but decided to finally provide a writeup about my setup. I had some extra hardware collecting dust in my office for a while, and decided to put it to use. For the past few years, I have been working on increasing the functionality and security of my own home network. My original “home lab” slowly turned into “home production” and my family and I have grown to rely on the infrastructure 24x7. This meant that my ability to test (break things) was now extremely limited.
I began looking for inspiration across the Internet to see what others have built. Although there are many online resources discussing security-specific homelabs, my interests in OT/ICS security led me to look for blogs with OT specific components. I came across two great resources: Rodrigo Cantera’s Website and Shaunna’s Youtube Page. Rodrigo provides an in-depth walkthrough of not only his lab setup, but also provides a very detailed walkthrough of using Scapy to conduct a process interruption attack through Modbus coil injection. Shaunna provided an excellent video which walked through a similar architecture and attack, this time using Metasploit to interrupt the factory process. These both gave me great ideas for the foundation of my architecture.
I then moved on to some more generic resources to provide some more depth to my environment. This guide to a Blue Team lab is very detailed and provided some great instructions on setting up a Windows Enterprise environment, which is something I definitely wanted to include in my setup.
Now that I had some good ideas in my head, I started thinking about my design. Since I knew I wanted to incorporate Facotory.IO into the setup, I thought about some of the industrial networks that I had worked with before. Additionally, I referred to some of the reference architecture in NIST SP 800-83R3 which was updated recently in September 2023. The major components of my network would include:
- Windows Server (Domain Controller with Active Directory, DHCP, DNS)
- Windows Clients
- OpenPLC
- Scada LTS
- Mitre Caldera for OT
- New subnet of my home network (but behind another firewall)
I began by drawing a physical layer diagram of how I would set this network up. To start, I looked at the three physical devices I would be using. First was a custom 1U server that I built and originally planned to replace my existing Nexcom NDIS B533 OPNsense firewall. Here I installed Proxmox and ran a virtual OPNsense firewall/router, as well as some DMZ machines, Metasploitable2 web server from Vulnhub and an Ubuntu workstation. I also had an extra Nexcom NDIS B533 (E-Bay sale and one of my favorite devices, a fanless digital signage computer with 2 Intel NICs – currently have one running my production OPNsense firewall). Once again, I installed Proxmox and setup a simulated Windows Enterprise environment, as well as some additional VMs. Finally, I had an Intel NUC that I used to run Factory.IO.
My goals of this exercise were to develop some additional hands on experience with attack/defense scenarios in the ICS/OT cybersecurity environment, increase proficiency with Windows AD security, and build out a completely independent test environement within my home network.